4 Ways Hackers Use Phishing to Launch Ransomware Attacks
Adrien Gendre
—September 12, 2019
—2 min read

MSPs have been on the receiving end of relentless ransomware attacks in 2019. In June, hackers infiltrated a number of MSPs via their Webroot management consoles. What followed was an all-out assault on MSPs and MSP client systems, with ransomware halting businesses, harming reputations, and even resulting in some high-value ransom payouts. In August, 22 Texas municipalities were hit with a ransomware attack that shuttered city operations, with one high-ranking mayor implicating the MSP.
Security analysts agree that most of these ransomware attacks were the result of compromised account credentials—usernames and passwords. Phishing is one of the top methods hackers use to compromise user accounts. These are the top four ways phishers gain access.
1. Inline Phishing Links
The hallmark of a phishing email is a link, but links are used in different ways and with a variety of obfuscation techniques. In the classic phishing attack, the phishing link leads to a webpage that impersonates a brand such as a vendor, cloud services provider like Microsoft and PayPal, or a bank. Phishing emails that drive users to webpages typically entice them by telling them their account is locked, their payment information is out of date or missing, or that they need to log in to retrieve a message or important document.
A popular version of this scam is the Microsoft OneDrive phishing attack. In these ransomware attacks, the user receives a spoofed email either from Microsoft or a colleague. The email directs the victim to click the link to retrieve a OneDrive file—but to do so, they need to login to Office 365. Once they do, their credentials are stolen.
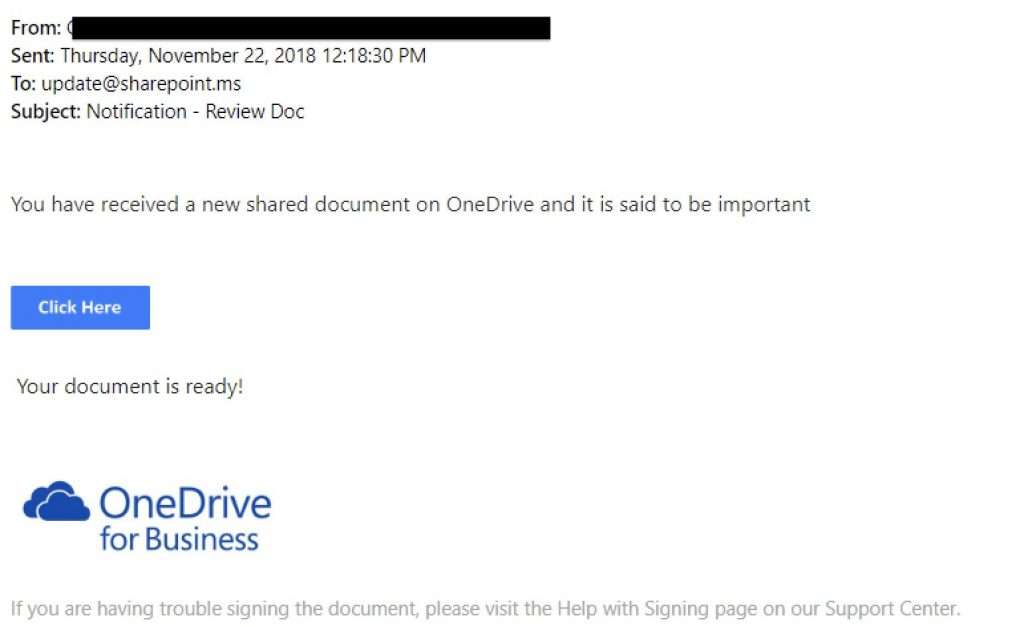
[Related] Office 365 Email Attacks: How Hackers Get Access to Your Business
2. Links in Attachments
To avoid detection from email security filters, hackers will place phishing links in attachments rather than the body of the email. A common phishing scam that uses fake attachments is the “Invoice Attached” scam. The phishing email directs the victim to open an attachment to retrieve an invoice. The invoice itself includes a link that leads to a phishing page, where the user inadvertently hands over their account credentials.
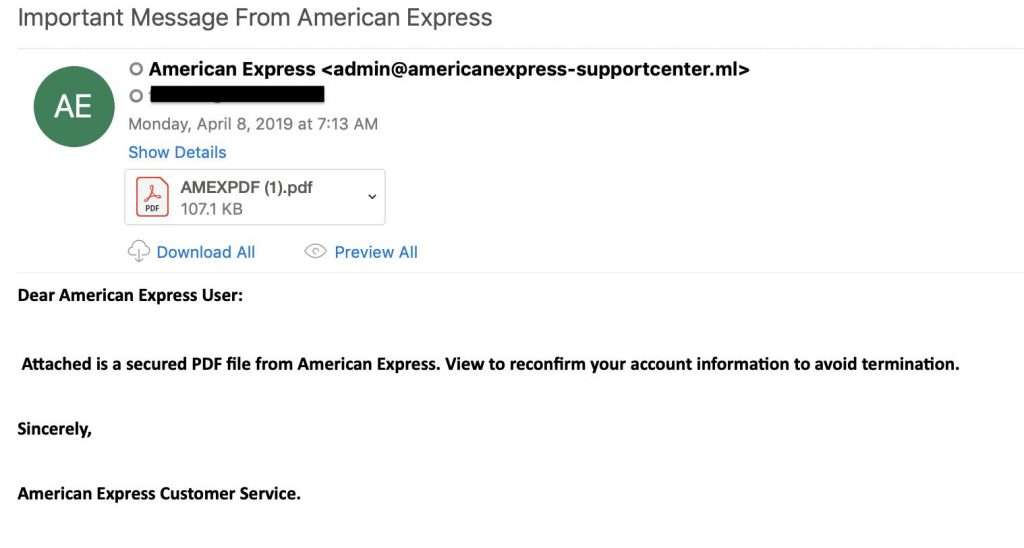
3. Fake Attachments
In these ransomware attacks, the email attachment—typically a Word doc or PDF—isn’t an attachment but a phishing link. When the victim clicks to open the attachment, they are directed to a phishing page. In other cases, the ransomware download begins automatically via a macro function or the victim enables macros in the document, which triggers the ransomware download.
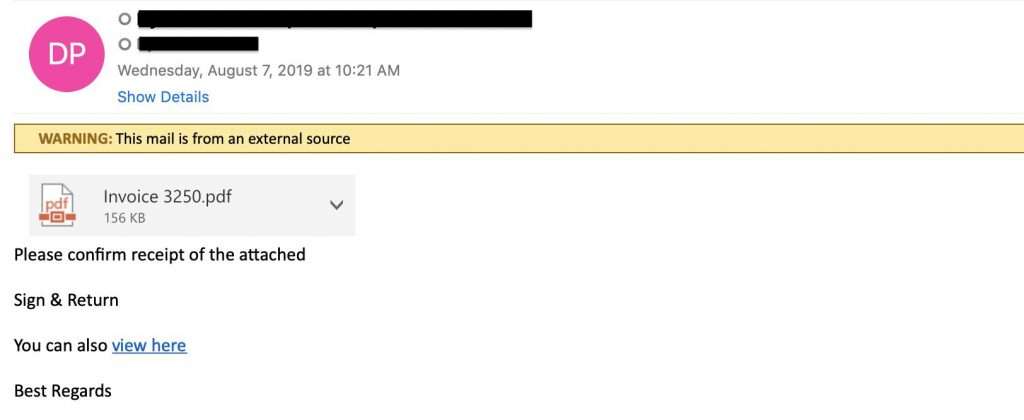
4. Multi-phase Attacks
A multi-phase or lateral phishing attack begins with phishing and evolves into spear phishing. In this attack, a hacker sends a spoofed Microsoft email asking the user to log in to Office 365. Once the user’s credentials are scraped on the phishing page, the hacker has access to the business’s Office 365 environment. Now, the hacker can send internal spear phishing emails throughout the organization.
For an MSP, a multi-phase attack has the potential to reach outside their organization and into their clients’ businesses. A hacker armed with a legitimate Office 365 email address can impersonate an MSP staff member and send emails to the MSP’s clients. This could be a phishing email asking the client to log in to one of their own systems or spear phishing emails that include ransomware-laden email attachments.
[White Paper] Office 365 Email Security: It’s Broken. Here’s How to Fix It.
Protecting Your Business and Your MSP Clients
Large enterprises have security budgets and capabilities that are out of the question for most SMBs. Hackers know this. They’re exploiting this by going after MSPs and launching ransomware attacks. Those who use Office 365 need an added layer of protection beyond Exchange Online Protection (EOP). Secure email gateways (SEG), once the standard in email protection, sit outside Office 365. This architectural limitation disables EOP’s signature-based protection—the primary method of detecting known ransomware. Consider a native, API-based solution that sits inside Office 365 and complements rather than limits EOP. A fully integrated solution simplifies configuration, goes beyond signature-based detection, and protects from insider spear phishing attacks.
Watch the 2-minute video to learn about our machine-learning based phishing protection for Office 365.




