5 Phishing Scams and How to Spot Them
Adrien Gendre
—February 20, 2020
—3 min read

Phishing scams are getting harder to spot due to increasingly sophisticated techniques designed to bypass identification from users and email filters. Most, however, follow a similar formula and contain the same elements. Here are five types of scams to watch out for:
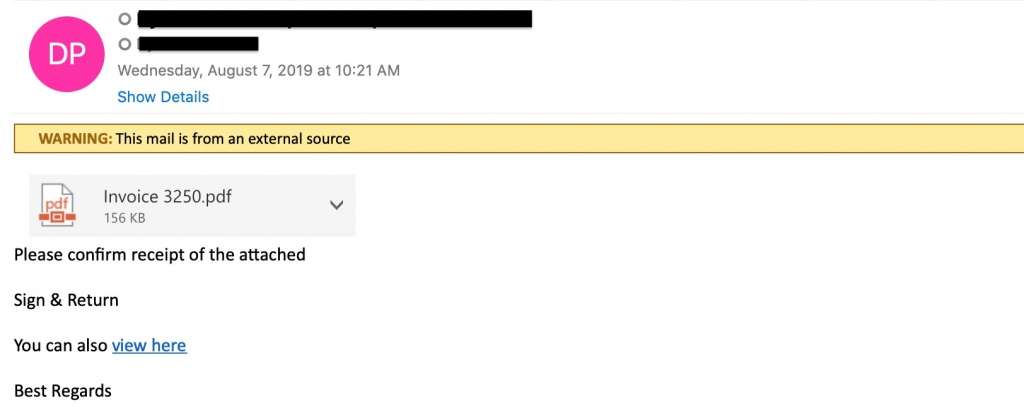
1. Invoice phishing scams
Invoice phishing involves spoofing a colleague, vendor, or brand. The email alerts the user that an important invoice is attached. The invoice itself might include a link to a phishing page where the user is directed to log in to pay an invoice. Or the attachment is packed with malware or ransomware, which downloads upon opening the attachment.
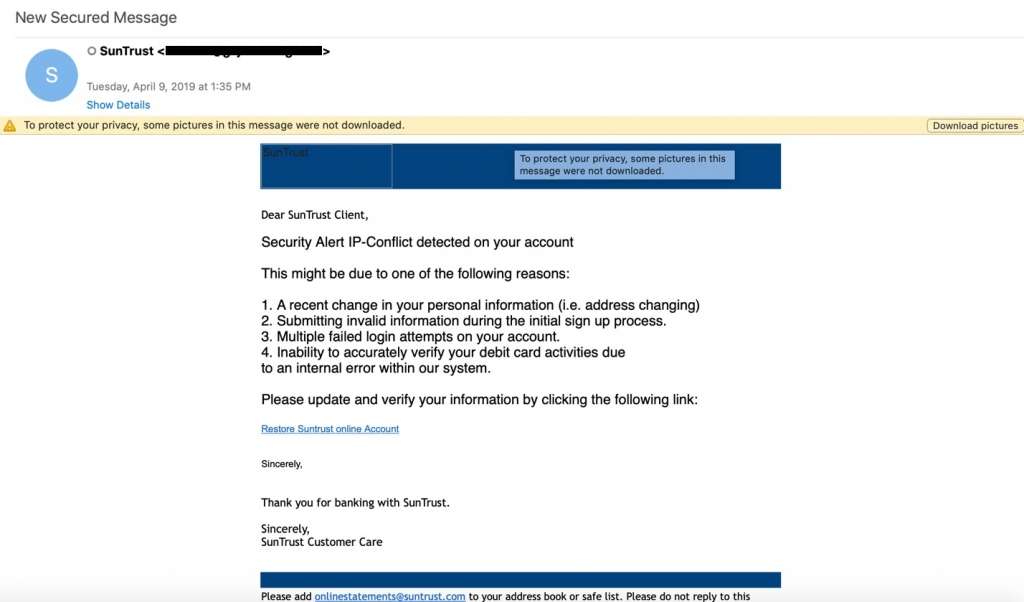
2. Security alerts
Security alerts from software and app vendors are a daily occurrence, but alerts from banks, cloud services companies, and email providers are especially troubling in business. In these phishing scams, hackers construct their phishing emails to look like legitimate security alerts that victims have seen before.
Common security alerts include warnings that a password has expired or is about to expire, that suspicious activity has been detected on an account, or that someone has logged in to an account from an unknown device. The purpose of these scams is to cause the victim to react quickly—to click the link in the email and log into their account to correct the issue. The victim believes they are protecting the business, when in reality they are doing the opposite.
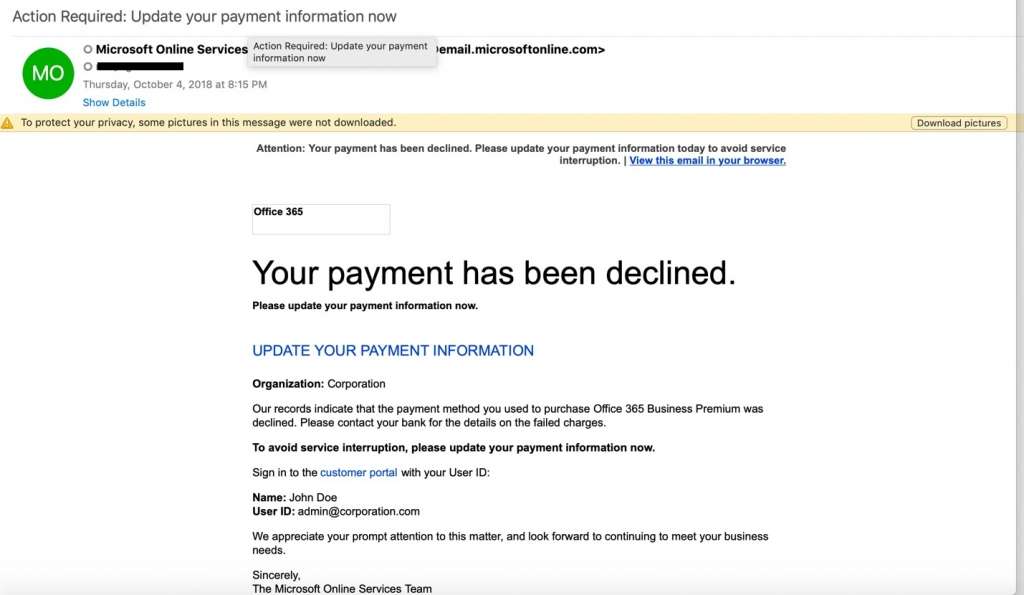
3. Update payment alerts
In the business world, a service outage of any kind can result in loss of revenue, IT downtime, and even customer churn if outages are a recurring issue. That’s what makes update payment phishing scams so effective, and hackers turn to it time and again to create that gut reaction they’re looking for in victims.
The email recipient is warned that their credit card has or is about to expire, or that there is an issue with their form of payment. They’re instructed to log in to their account to update their credit card. In sophisticated attacks, hackers will research the company and identify an employee who is likely to be responsible for keeping accounts current.
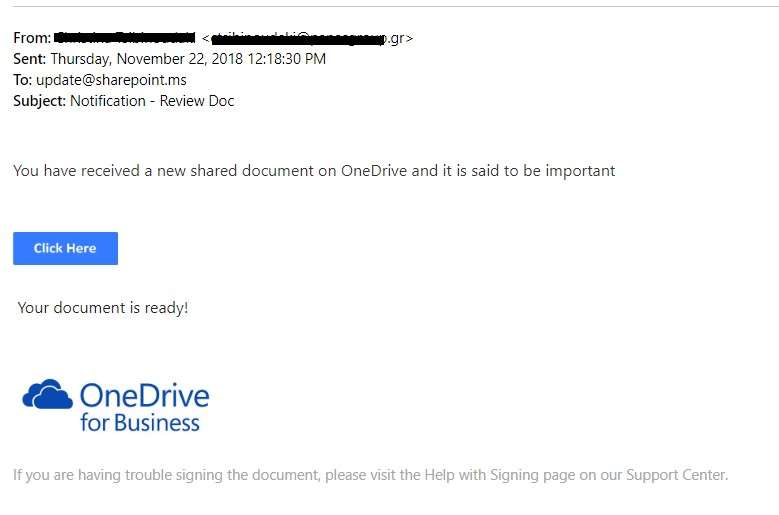
4. Shared-file attacks
The popularity of cloud services like Office 365 has created a host of new opportunities for cybercriminals. Businesses around the world are increasingly sharing files directly from hosting services like SharePoint and OneDrive.
These phishing scams involve sending a fake SharePoint or OneDrive notification, along with a link to view the document, which includes a phishing link. In these scams, hackers spoof the email address of a colleague or business partner. In more sophisticated Office 365 attacks, hackers generate real SharePoint and OneDrive notifications via Office 365. In even more advanced attacks, hackers generate notifications through compromised Office 365 accounts.
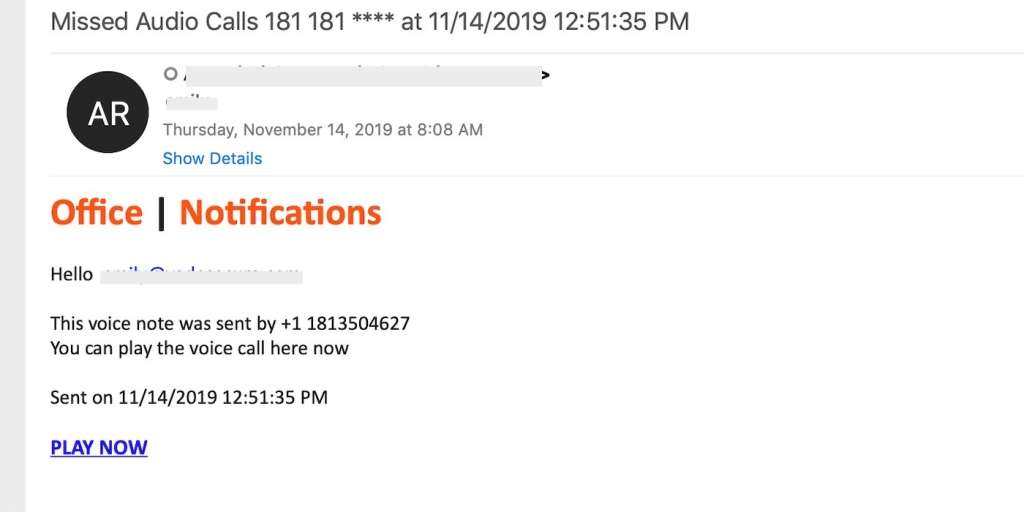
5. Voicemail phishing
Voicemail phishing emails are typically brief and alert recipients that they have received a new voicemail. These types of phishing emails often originate from email addresses that are spoofed to look like legitimate notifications from services like Office 365. In those cases, the recipient is instructed to click a link to log in to their Office 365 account to listen to the voicemail.
In other cases, the voicemail is delivered in the form of an attachment that includes the phishing link. Voicemail phishing scams are also a popular method of delivering ransomware. The download could begin immediately upon opening the attachment, or the download could begin if/when the recipient agrees to enable macros in the document.
How to spot a phishing email
The signs of phishing scams are not as obvious as they once were. Hackers take great care to conceal the signs of phishing, and often the most obvious indicators are not visible without close inspection. Below are just a few ways you can spot a scam:
Consider the subject line: Would a reputable brand threaten you in the subject line of an email? Probably not. If the subject line seems threatening or dramatic, it could be a phishing scam.
Check the sender’s address: Does the sender’s email domain match that of the brand? Are there extra characters in the email address or extensions like .co or .company that shouldn’t be there? Scrutinize the sender’s address, and look for signs of email spoofing before clicking any links.
Look for personalization: Any business sending you correspondence should know your first name. If you are addressed by anything other than your name, such as Dear User or simply Hello, then you should consider the email suspicious.
Hover over links: Hover over links in the email to ensure it leads where it should. Often, phishing links will be long and complex with an excess of special characters. If it’s not clear where they link leads, do not click on it.
Check the brand’s website: If you’re unsure about a link, type the brand’s website directly in your browser instead of clicking. Or use a free service like IsItPhishing.AI to scan the URL for phishing.



